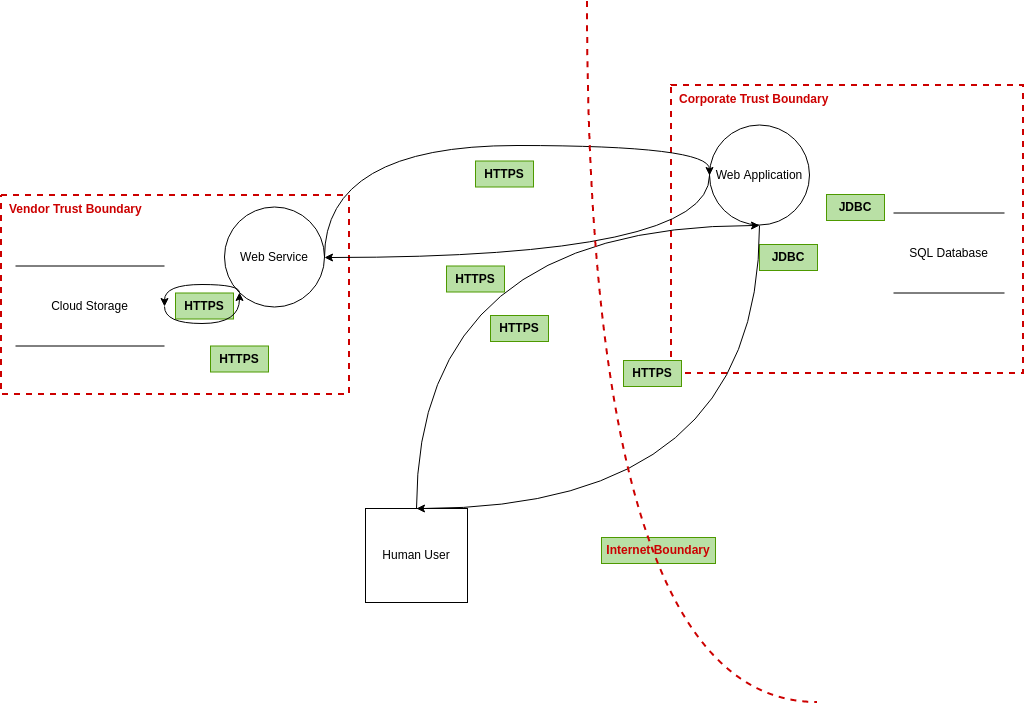
1.4 cobots guidance - threat modelling - Assuring Autonomy International Programme, University of York
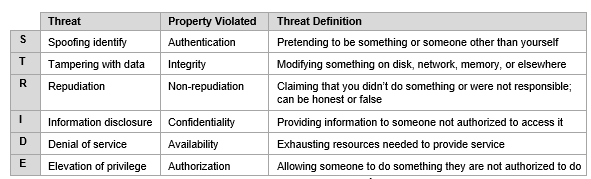
![PDF] A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security | Semantic Scholar PDF] A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c38ea87c76d6aa5afaa8311f592bc3daf5a4d7c2/2-Figure1-1.png)
PDF] A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security | Semantic Scholar
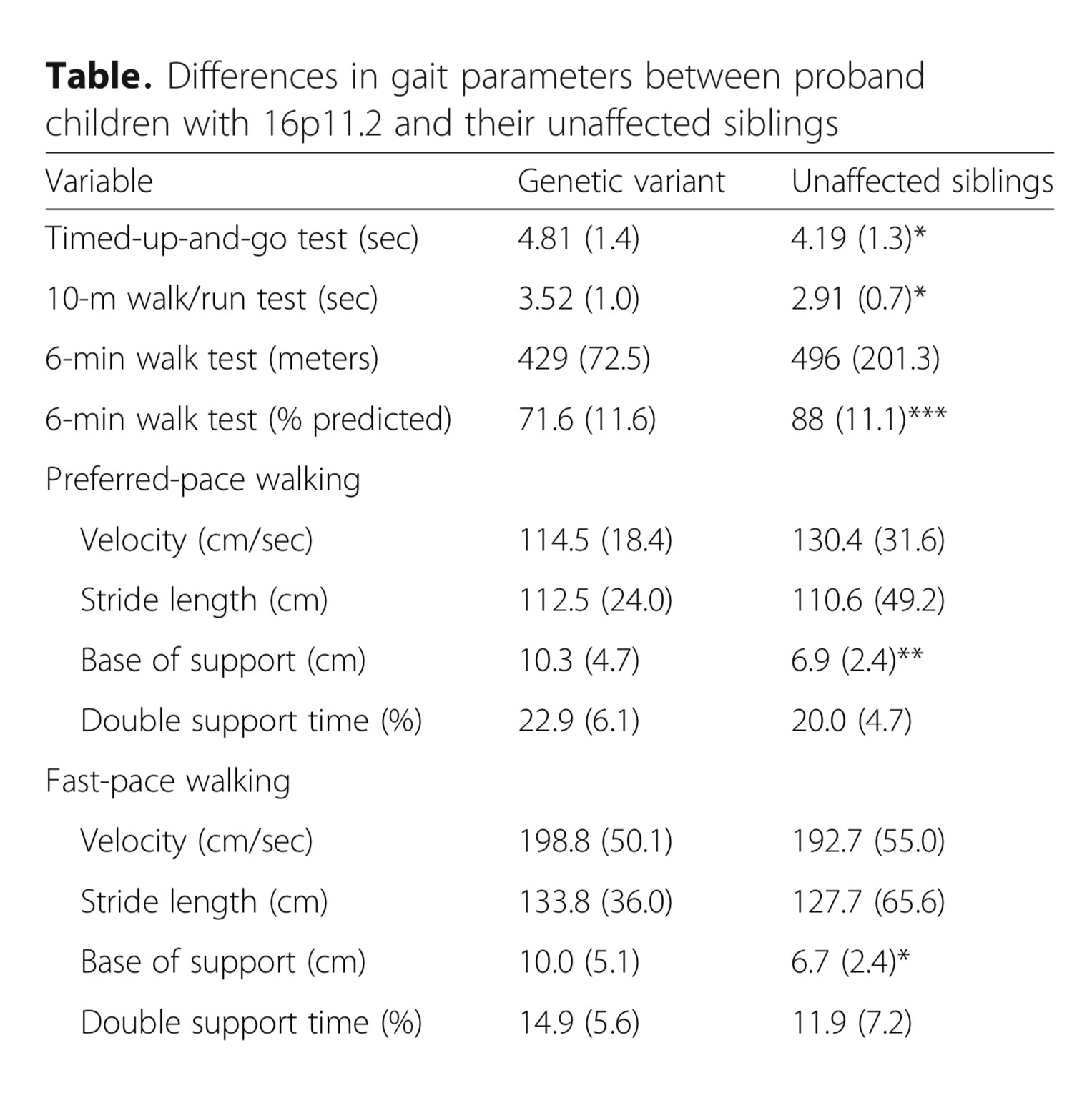
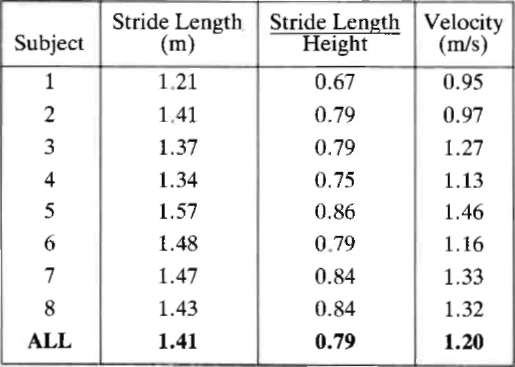
Steps to Take to Enhance Gait Stability: The Effect of Stride Frequency, Stride Length, and Walking Speed on Local Dynamic Stability and Margins of Stability | PLOS ONE